Public key authentication can provide more secure login than password authentication. With public-key authentication you generate a key pair to use to validate your identity instead of using a shared password that both you and the host know. The server is given your public key, and possession of the private key is enough to prove your identity for login. As with public key encryption, this security model hinges on your ability to keep the private key private. Private keys, however, are often written to files. Sometimes these files are password encrypted and sometimes there not. With today’s threats that include viruses, malicious Trojans, and key loggers, these private keys may be at risk, even the password protected ones. They can be stolen, copied or otherwise hijacked, thwarting your security efforts.
This is where Smart Cards and Smart Tokens come into play. These handy little devices include CPUs and built-in encryption hardware. The sensitive parts of the authentication occur IN THE SMARTCARD!! The private key is generated within the token and can’t be copied because it never leaves the device. Attempts to pry the device open to access the hardware inside will destroy the device, rendering the private key unreadable. Physical possession of the smartcard is a guarantee that you possess the private key (and no one else does). This is the same technology now being employed by banks in your chip-enabled credit cards and the same technology used by the Department of Defense in their CAC (Common Access Card).
Below, you will find the steps needed to attain this level of security for your own servers without a huge investment in hardware and infrastructure.
In this example, I’ll give you step by step instructions to implement SSH smartcard authentication using a commonly available USB-based smart token called PIVKEY. USB-based smart tokens work the same way as smart cards, but you get to skip the step of installing a card reader. All you need is an available USB port. This example is done using AbsoluteTelnet 10.15, though Absolute has supported smartcard authentication in various forms since version 4. I’m using Windows 7, though I’ve verified this also works with Windows 10. If you use something other than the PIVKEY, the driver download step will be different but most of the other steps should be pretty similar regardless of the device you use. I’ll try to post information about other supported devices as I test them.
- Purchase a token. In this example, we’ll use the PIVKEY token, purchased from amazon.

2)Download pivkey admin tools here
3) .Install PIVKey Administrator from the zip file above, taking all of the default options. vSEC CMS can also be installed to perform operations such as changing the PIN on the card.
4) Insert your PIVKEY token into an available USB slot. Give windows a few minutes to download and install additional drivers
5) Download, install, and run AbsoluteTelnet/SSH from (https://www.celestialsoftware.net)
6) On the Options->properties->Connection->SSH2 tab, enter the hostname and port number of your server and enable ‘use smart card or USB token’
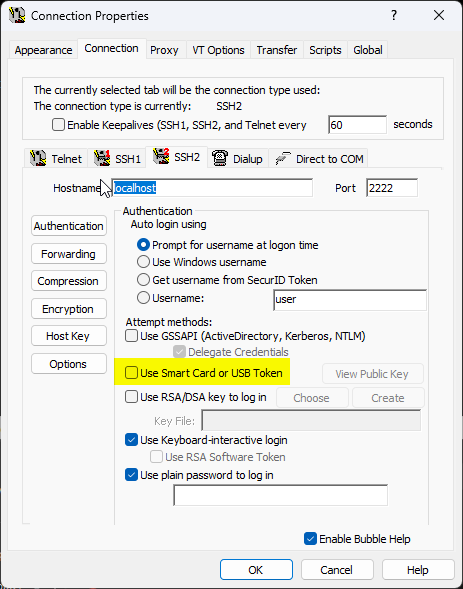
7) With the PIVKEY token still inserted, click ‘View Public Key’ This will bring up details of your public key and some instructions on how to install the public key to your server. These instructions may be different depending on type type of server you’re using. For OpenSSH, it’s as simple as appending the key to your authorized_keys file. This may require you to email the public key to your server admin or make one last connection using your password in another session to append the public key there. If you’ve used file-based public-key authentication, you should be familiar with this part as it is the same.
8) Once the public key has been installed on the server, you’re ready to login with the smartcard. Back at the main AbsoluteTelnet/SSH screen, click the connect button to start the connection. When prompted, enter your username and the PIVKEY pin (default 000000 if you haven’t changed it) Subsequent logins will not require you to re-enter the pin unless you remove and reinsert the token.
Email me if you have further questions: